
| Resurrection Home | Previous issue | Next issue | View Original Cover | PDF Version |
Computer
RESURRECTION
The Bulletin of the Computer Conservation Society
ISSN 0958-7403
Number 46 |
Spring 2009 |
| IMechE Engineering Heritage Award for the Bombe | David Hartley & Dik Leatherdale |
| Editor’s Remarks | Dik Leatherdale |
| News Round-Up | |
| Society Activity | |
| Pioneer Profiles - Stan Gill | David Barron |
| Some More CAFS Applications | Hamish Carmichael & Martin Wright |
| Preserving an ICT 1301 | Rod Brown |
| Kings College London Computing Museum | Richard E. Overill & Jantje A. M. Silomon |
| The Prime of Life | Simon Lavington collection |
| Obituary: Harry Johnson | Hugh McGregor Ross |
| Obituary: Brian Napper | Dik Leatherdale |
| Forthcoming Events | |
| Committee of the Society | |
| Aims and Objectives |
| Top | Previous | Next |

In 2009, it is possible to buy a computer in which the only moving parts are the keyboard and the off switch - not even a disc. But it was not always so. In the Victorian era, Babbage’s calculating engines were entirely mechanical in nature. By the early 20th century, machines combining complex mechanical engineering with novel electronics handled a little of what we now call information technology. And one of the most sophisticated of these hybrid machines was the “Bombe” developed by Alan Turing and Gordon Welchman and manufactured in Letchworth by the British Tabulating Machine Company for the purpose of breaking the German Enigma codes.
So it is appropriate, if on the face of it, a little unexpected, that the latest Engineering Heritage Award given by the Institution of Mechanical Engineers (IMechE) should recognise this outstanding achievement; not only of the original designers and builders, but also of the team which has heroically and painstakingly reconstructed one of these seminal machines over the last decade and more. This despite the destruction of the original machines and much of the information about them ordered by Churchill in 1945.
At a ceremony on 24th March attended by Society Chairman David Hartley and BCS Deputy President Elizabeth Sparrow, John Harper accepted the Award on behalf of the team he has for so long led. In his response, John paid tribute to all those who have contributed and to the pioneers of so long ago.
Readers of Resurrection have followed the progress of the replica Bombe these many years past and cannot fail to have been impressed by the skills, commitment and sheer tenacity of everybody involved.
The Computer Conservation Society congratulates the Bombe team on this signal honour. Long may they continue!

The award ceremony - L→R David Hartley, Elizabeth Sparrow John Harper, Isobel Pollock - Chair of IMechE Heritage Awards Committee, Norman Dawson (who recommended our machine to the IMechE Awards committee), Simon Greenish - Director Bletchley Park Trust
| Top | Previous | Next |
This month’s profile is of one of the early Presidents of the British Computer Society, Stan Gill. Prof. Gill sadly died young in 1975, well before the age of the World Wide Web, but not so long ago, that it can conventionally be considered as “history”. So David Barron has had to overcome considerable difficulty in researching his life. The distinguished political journalist Alan Watkins was fond of saying that “There are no times so obscure as the day before yesterday”. I’m coming to understand what he meant.
One of our feature articles in this edition is from Rod Brown, a member of the group restoring an ICT 1301. Rod tells us about the machine and its history as well as the restoration. Above all, he makes it all sound like so much fun! His enthusiasm is infectious. That is as it should be. Unless we enjoy what we’re doing, our tasks will, inevitably, fail. You will also read that the 1301 Group is joining forces with the Computer Conservation Society to our mutual benefit. We can, perhaps, help and inspire one another.
One of the unforeseen joys of being editor of Resurrection is the opportunity to meet colleagues of long ago and to make new contacts with people from the industry in which we have all toiled. Recently, I was able to find a home for some rare Apple computers in the keeping of a friend from my distant student days, simply by putting him in contact with another colleague. Connecting readers to one another is one of the great pleasures of the job. Last week, I introduced two people with a common interest. They already knew one another, but had no idea that they had that interest in common!
Some time ago, we invited readers to say how they would like to receive Resurrection. A small number said they would like to forgo their paper copy in favour of reading it on the Society website. Having discovered and validated a means of achieving non-delivery, I can now offer readers who email me, the option of not receiving a paper copy. Instead, as soon as Resurrection appears on the website (often some weeks later I have to warn you) I will email them to let them know.
| Top | Previous | Next |
Repairs to the roof of the mansion at Bletchley Park are now complete and some more general repairs are being carried out on the building and around the estate. Milton Keynes Council have contributed a further £300,000, releasing funding previously allocated by English Heritage. It is particularly pleasing that the grant from Milton Keynes was the result of a vote by local residents.
The Save Bletchley Park e-petition was hovering at around 20,000 signatures as Resurrection went to press. At one stage, it climbed to third position in the list of petitions vying for the attention of the Prime Minister. The petition closes towards the end of May.
12th July will see a visit to Bletchley Park by the BBC’s popular Antiques Roadshow. Transmission date is not yet known.
-101010101-
On the evening of 20th March, The National Museum of Computing hosted the premier of Obsolete?, an electronic musical work by Matthew Applegate (aka Pixelh8), featuring the sound of more than 20 of the Museum’s vintage computers. During an afternoon visit, the Elliot 803 was heard to be playing Elizabethan Serenade by Ronald Binge. Limbering up, perhaps?
-101010101-
2012 marks the centenary of the birth of Alan Turing. The event will be commemorated around the world. www.turingcentenary.eu may be consulted for details, though plans are still in their early stages as yet.
-101010101-
Congratulations to Prof. Brian Randall on his appointment as a Fellow of the ACM “for contributions to dependable computing and computer history”.
-101010101-
The Society has its own Web site, which is now located at www.computerconservationsociety.org. It contains news items, details of forthcoming events, and also electronic copies of all past issues of Resurrection, in both HTML and PDF formats, which can be downloaded for printing. We also have an FTP site at ftp.cs.man.ac.uk/pub/CCS-Archive, where there is other material for downloading including simulators for historic machines. Please note that the latter URL is case-sensitive.
| Top | Previous | Next |
1301 Project Joins the CCS!
On the 12th March, the 1301 Project, which is described elsewhere in this edition of Resurrection, was welcomed into the CCS fold. It formally becomes a working party of the Society and its representative, Rod Brown, is appointed to our Committee. Chairman, David Hartley opined “This completes an important piece of unfinished business for the CCS. Discussions started some years ago for the CCS and the 1301 Project to come together, but this was delayed by other events. I am pleased that we have, at last, completed the process. The CCS Committee is delighted to welcome this imaginative project into the fold, and we are also delighted that the feelings are reciprocated by Rod Brown and the owner of the 1301, Roger Holmes.”
Software Preservation
David Holdsworth
There is a flurry of activity that has arisen around KDF9 as a spin off from the “Our Computer Heritage” project. We only have scraps of software, but would love to get hands on more: listings, paper tapes, even magnetic tapes.
At present we have:
We are collecting material on a website: sw.ccs.bcs.org/KDF9.
What we would also like to have is documentation of the parts of the order code that are not on the above website. This particularly relates to a revision of the mnemonics for the peripheral instructions that happened about the time that KDF9s were getting disc drives. For example, the rather descriptive mnemonic MFR (for magtape forward read) was replaced by PIA with the claim that is was simpler. Simpler for writing the assembler, not for understanding someone else′s code! More detail on how the disc drive instructions worked is being researched.
Bill Findlay is working on an interpreter, and I am working on an assembler/analysis tool, as an aid to cleaning up the manually created source listing of the director.
The web material includes a 1969 paper describing the KDF9 system at Leeds University.
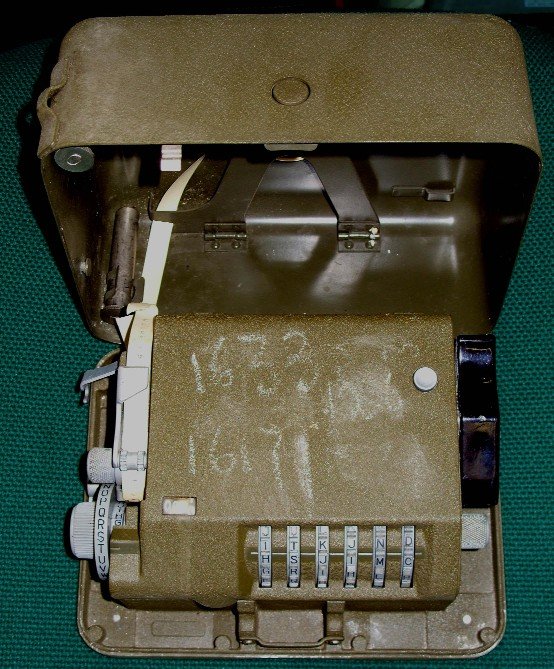
Bombe Rebuild Project
John Harper
Supporters will be pleased to hear that we have received further generous donations to complete our extra drums. However we still need to raise £1,400 to complete the 40 additional drums. The three versions for the Checking machine are already complete and tested.
The Consecutive Stecker Knock Out
In Resurrection 45 , I mentioned an extra diagonal board that we were making. This is now complete and fully tested. We have proved to our own satisfaction that the two extra features function as they did in WWII.
The Diagonal Board was the inspiration of Gordon Welchman and proved to be a great asset as it eliminated many false stops on a weak menu. In doing so, it made the application of less complex menus more effective with a consequential saving in time, effort and wear and tear.
What is less well known is that further improvements took place. One of these was called the Consecutive Stecker Knock Out (CSKO). The other feature to report on is the Single Self Stecker (S.S.S.) feature. This I will cover in the next Resurrection.
It had been observed that on some enemy networks they had a rule not to use consecutive letters for steckers, e.g. they would not use either A or C as a stecker for B. In breaking traffic from these networks, stops which include such consecutive steckers can be rejected so as not to cause false stops if the self steckers were all connected together. A voltage on any consecutive stecker link will then be applied to the whole menu and an invalid open circuit appearing at the sense relays would be eliminated.
All consecutive steckers are wired together on the standard diagonal board such as aB, bC etc. to yZ. To these two point links, we have added extra wires and these have been brought out to an additional 26 way jack. The connection is done automatically by the use of the CSKO jack which causes the bombe to reject such stops and continue testing. An ‘EEL’ plug inserted in the CSKO socket has all 26 points connected together, thus voltage on any one link is applied to all the others. An EEL plug is a WWII item that we made previously. It allows any combination of connections to be made using a daisy chain of plugs on the same single wire
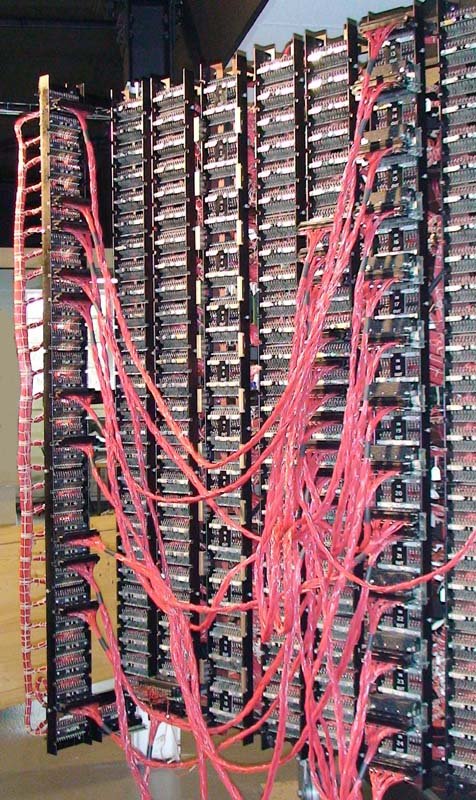
40 out of the 210 machines were fitted with this feature. There was no particular pattern of when this feature was fitted but there does appear to be a concentration on machines delivered in 1942 and 1944 and in particular to those initially delivered to outstations Wavendon and Eastcote.
However it was fitted to machines of all types, the first being fitted to number 7 delivered in August 1941.
Testing completed so far shows that as many as half of the false stops can be eliminated. It is therefore a very useful feature when finding the settings on German networks that used the ‘no consecutive stecker’ rule.
This view shows the jack frame gate with the additional Diagonal Board mounted at right angles on the left on temporary brackets. It can be quickly removed by loosening three clamps for such things as authentic filming. The two extra jacks can be seen at the bottom. A closer view will be shown in my next article.
Our website is still at https://www.bombe.org.uk/
| Top | Previous | Next |

To some of us of a certain age, Stan Gill will be remembered forever as the ‘G’ of ‘WWG’ - Wilkes, Wheeler and Gill, the classic first ever book on programming which was a guide to programming the EDSAC 1 and its extensive library of subroutines. For that achievement alone, he deserves a place in the pantheon of computing. I personally have particular reason to remember the subroutine that implemented the Runge-Kutta-Gill (RKG) method for the integration of ordinary differential equations, which was a cornerstone of my research in the Cavendish. RKG was distinctly faster than the classic Runge- Kutta method, and on a seriously slow machine like the EDSAC 1, that was a great benefit. (Indeed, it only took twenty minutes to compute the next point on the graph!) Incidentally, the RKG subroutine took as one of its parameters the address of another subroutine: the very first instance of a formal function.
Stan Gill, born 26 March 1926, attended Worthing High School from 1935 to 1943, and from there went to St John′s College, Cambridge from 1943 to1945. At the time, students were allowed two years of undergraduate study before doing National Service. Fortunately, as part of his national Service, in 1946 he was posted to the National Physical Laboratory (NPL) as a Temporary Assistant Experimental Officer working on the design of the Pilot ACE, and the following year he became an Assistant Experimental Officer developing a Test Assembly as part of the ACE feasibility study. In October 1948 he returned to St John’s to take Part II Physics (having already taken Part II Mathematics). In the 1949 Long Vacation he returned to NPL for a couple of months before joining Maurice Wilkes as the second research student in the Cambridge Mathematical Laboratory (David Wheeler was the first). This made him one of the few people (only person?) to have worked both with Alan Turing and Maurice Wilkes. His formal research was on the numerical solution of differential equations (see personal comment above), but he also played a substantial role in the development of the EDSAC 1 programming system and its library of subroutines (hence his co-authorship of WWG). From 1952 to 1955 he was a Research Fellow of St John’s College, Cambridge, and from 1954 to 1955 he was Visiting Assistant Professor at the University of Illinois, following in David Wheeler’s footsteps.
In 1955 he moved to the computer department of Ferranti Ltd (later ICT) in Manchester, staying until 1964 and taking a leading part in the development of the commercial version of the Manchester Atlas computer. During that period he was also appointed part-time Professor of Automatic Data Processing at UMIST. That can’t have been a easy relationship - there was a certain rivalry between Cambridge and Manchester at the time and some distance between UMIST and Manchester University, home of all the computer development. And it probably didn’t help when Stan wrote an internal Ferranti technical memo explaining why paging and automatic memory management was not a good idea!
In 1964 he was appointed Professor of Computing Science at Imperial College London, and in 1966 he became Director of the Centre for Computing and Automation at Imperial, a position that he held until 1970. The arrival of a new Head of Department led to tensions in the Department and in 1970 he left to become Director of various companies in the Miles Roman Group. In 1962 he became a Senior Consultant with PA International Management Consultants Limited, a post which he held until his death in 1975. (He once remarked to me that PA Consulting had appointed him “to add tone to the establishment”.)
During his career he acted as consultant to various organisations, in particular ICT and the Ministry of Technology. Of particular note is that he was the third President of the British Computer Society in the year 1967-1968.
His tragically early death at the age of 49 robbed us of a leading figure in the computing community. Who knows what he might have achieved if he had survived? He was a gentle man, always willing to help and advise the next generation. (Though as Maurice Wilkes recalled, “occasionally, when he felt strongly ... he could show a degree of forcefulness that took some by surprise”.)
He carried his talent and learning with great modesty. So, more than thirty years on, RIP, Stan.
Postscript. I have been greatly assisted in preparing this piece by the ‘Personal Memoir’ of Stan written by Maurice Wilkes for the Computer Bulletin in 1975. Normally I would have followed academic custom by citing this work. I have taken the liberty of just using the information. To Maurice, I say ‘mea culpa’ for this discourtesy.
| Top | Previous | Next |
We continue our account of ICL CAFS applications with INDEPOL, an intelligence- storage and retrieval application.
The reaction to Querymaster among the more advanced CAFS 800 users was loud and many-coloured. In particular, Defence users privately described the new software as a sharp step back into the Stone Age. But at a crucial meeting with Robb Wilmot, then ICL’s Managing Director, a wily senior RAF Group Captain mildly asked whether the new CAFS software would match the capabilities of what they were used to. Off guard, Robb blandly confirmed that it would. He was thus personally committed to making good a rash public assurance. When the dust eventually settled, we found that the Sales Division responsible for MoD business was charged with producing software which replicated all the good bits of the CAFS 800 package, plus online updating, plus a large number of other desiderata. It was the right decision, but took some years to achieve.
After initial design work, a development team was formed in Stevenage, including key members of the original CAFS development team, Defence sales and support teams, and people with detailed CAFS 800 experience - in fact anyone who might be useful and who wasn’t tainted with the Bracknell relational dogma. Space was provided, as was the necessary computer. By magic, normal budget approval processes seemed to be short-circuited by the need to make good Robb’s commitment.
Development was fast, but extremely well disciplined. Everything was held in the Data Dictionary System, which was used as the project repository and was constantly being updated. If something wasn’t in DDS it wasn’t kosher, and it certainly wasn’t part of the product. In retrospect the team remembers this as a time of the most intense effort, when engineering principles dominated, and conventional procedural rules were ignored. But it certainly worked, and worked well enough to suggest that the conventional procedural rules were perhaps unnecessary.
The time came when the development task seemed to have outgrown the capabilities of the in-house team, so various software houses were invited to bid for the work of completing the job. A contract was awarded and work continued, but it soon became apparent that the software house way of doing things was totally unsuitable, so we poached the software house staff who now knew the basis of the product, brought the work back in-house, and completed it ourselves.
When completed the software was given the name ‘INDEPOL’, standing for INtelligence in DEfence and POLice. Its origins in the defence world explained the strength of the security facilities, which favoured its subsequent adoption in a variety of very sensitive application areas.
Under the surface INDEPOL was technically an interpreter: no part of an INDEPOL application was compiled. The details of what was required were held in a System Model and a Data Model. The latter described the files, records and fields to be searched and updated, using a pragmatic subset of the principles of the Associative Data Model which had grown up with the original CAFS.
The System Model held material at three levels: System, Application, and User.
All parts of an application could be developed online by a user with sufficient permissions. Within limits, each user could personalise his profile to suit his particular style.
INDEPOL applications
Many of ICL’s own internal systems quickly became accessible through INDEPOL. Indeed, the availability of INDEPOL enquiry facilities considerably accelerated the migration of those systems to the VME environment, since so many report programs did not need to be re-written.
Responsibility for INDEPOL’s maintenance and development came to rest in ICL Defence Systems, where both authors latterly worked. It therefore made sense to use our own product for our own information requirements. Among the applications were bug-tracking, change control, prospect intelligence, competitive information, and details of forthcoming customer/prospect visits. Holding the product’s manuals online made it much easier to ensure that the text consistently reflected each enhancement to the facilities.
Across the police world in general systems were developed to handle incident recording, criminal intelligence, organised crime, drugs trafficking, firearms and shotguns, and vehicles of interest. It was unfortunate that at the time there was little commonality between the computer systems used by UK police forces; each force took its own line and, it appeared to us, seemed deliberately to avoid doing things in the same way as its neighbours. When the Home Office tried to impose standards, the effect was not usually successful.
Lancashire Constabulary developed a straightforward and robust incident logging system, and rapidly made it available throughout the force. The value of having searchable text was well illustrated early on, when a quick scan of the M.O. (modus operandi) text fields put an end to the activities of one prolific family whose speciality was squirting quick-setting foam into the burglar alarm before breaking into the off-licence it was protecting.
We later had an agreement with Lancashire Police to sell their system on to other users, the effect of which will be described later.
Across the Pennines, North Yorkshire Police, based on several years experience with CAFS 800, built a much more sophisticated Intelligence Recording System. They had a particularly brilliant IT man who could make INDEPOL play tricks even we had never thought of.
Because crime doesn’t respect police force boundaries, the North Yorkshire system became a de facto regional intelligence system, with terminals connected to it from police forces in West Yorkshire, South Yorkshire, Cleveland and others. This was achieved by low-level collaboration between the participating intelligence analysts, who liked what the North Yorkshire system did and wanted to take advantage of it. It would not have been possible to achieve the same integration by getting the Chief Constables to agree, and certainly not by forcing the respective IT managers to adopt a common policy
In complete contrast, the Northern Constabulary was a rather surprising devotee of INDEPOL. Hamish Carmichael well remembers, on his first visit to headquarters in Inverness, Chief Superintendent George Henderson saying: “You must realise, Hamish, that crime up here is not at all like what you’re used to down south. We know perfectly well that if we arrested 12 people on the mainland, and another six - or, no, maybe seven - on Orkney, crime would stop! And then where would we be? Look at all these figures we have to send in to Edinburgh: number of crimes committed - zero; number of crimes detected - zero; they’d be telling us we don’t need police stations in Wick or Thurso, and we’re not having that!!”
Northern Constabulary wanted a flexible system to cope with the large numbers of sporting guns being brought into its area. It was explained that more weapons pass through Inverness airport than through Heathrow, Gatwick, Luton and Stansted combined.
There was also an incident logging system, not a straight copy but based quite closely on Lancashire.
The British Transport Police likes to boast that it was the first police force in the world to use IT in the fight against crime. A man committed a murder in Berkshire, caught a London train in Slough, and thought he had got away with it. But the police telegraphed to Paddington with details of his distinctive overcoat. He was recognised, followed from that station to a hotel in the City and arrested there. That was in 1844!
Their INDEPOL information system was called PINS, and was used nationwide. BTP didn’t have to bother about the cost of BT lines: all their data traffic could piggyback on the network already installed for signalling and message traffic. Two areas where it was quickly very successful were against pick- pocketing gangs on the London Underground, and car thefts from commuter car parks around London.
The Royal Naval Supply and Transport Service (RNSTS) provides a total logistics service for the Royal Navy. Its main centre is at Ensleigh, near Bath, with main store bases and units across the UK and in Gibraltar. It even has terminals deep under ground in the old Bath stone quarries. In the mid-1980s it held 800,000 stock items and dealt with 4,500,000 issues per year. To cope with this load RNSTS had developed an excellent IDMSX-based inventory control system known as CRISP, which included some standard management information outputs, but the system was not good at ad-hoc queries. These could only be solved by hand- crafted COBOL programs which, at this time, had a six month backlog. Because of this delay, users were asking for more and more output from each request, just in case it might be needed.
INDEPOL was selected as a solution to the problem because of its rapid response, ease of use and simplicity of implementation. A team of four designed and implemented a pilot solution in a few weeks. The team was a mixture of RN and ICL personnel and Martin Wright was one of the team.
Files were copied from CRISP once a week, which was quite often enough for accurate management information. This process was also used as a time to add enhancements to the system. The project went from pilot to full-scale by the way of frequent small enhancements without any major quantum leaps.
Answers were now available in minutes rather than months, and were accurately aimed at the current problem - the rapier rather than the bludgeon.
Users were hooked on the system within days. One manager of contracts with Rolls Royce said that for the first time he was able to deal with the supplier on equal terms. The Royal Navy claimed savings of £2m in the first year in reduced stocks, improved repair times and elimination of duplications.
The army later installed a very similar system at RAOC Bicester.
The Royal Malaysia Police was quite secretive about its main INDEPOL applications. In any case when one visited all the screens were in Malay, which confirmed the language flexibility of INDEPOL but didn’t facilitate understanding. There was probably a great deal of secret intelligence work about the possibility of inter-communal violence. In addition they had a conventional incident recording system, and another major application was in the area of firearms.
They also showed the flexibility of the software by designing an intelligence system specially tailored to planning the protection of visiting VIPs during the CHOGM (Commonwealth Heads of Government Meeting) in Kuala Lumpur in 1989.
The Royal Hong Kong Police has a long history of having to cope with organised crime in the form of the Triads, who still trade on their origin several centuries ago as patriotic societies, though their current activities are nasty and brutal in the extreme. In this country the Met and the Greater Manchester Police know them only too well.
Our main contact in Hong Kong was a British Detective Chief Superintendent, a giant of a man, ex-Guards and erect as a lamp-post. When his tour of duty in Hong Kong was over he joined us in UK to continue his work in anti-Triad intelligence. He very effectively used INDEPOL to collate information on various forms of Triad activity - loan-sharking, protection money, blackmail and the like.
Apart from police work in the colony, RHKP was involved in a lot of collaboration - e.g. with the Met and with the Australian Federal Police.
RHKP also introduced us to Anacapa link-charting. (Anacapa was a small software company in California who developed a very successful set of rules for depicting the connections involved in criminal activity in graphical form.) Link-charts proved to be an extremely effective way of presenting in court evidence of complicated networks of criminal activity.
(It is not directly part of the CAFS story, but as a result of the Anacapa work in Hong Kong an ICL team developed a very effective Intelligence Analyst’s Workstation, to help to generate the link-charts online. Its use proved invaluable when the Lancashire Constabulary was faced with a murder perpetrated by an international gang of fraudsters: a four-year investigation involved collaboration with many overseas police forces, and the records of direct relevance included 7300 people, 6200 addresses, 6700 events, nearly 10000 telephone calls, and over 15000 other records. Without IAW it would have been impossible to keep this mass of information under control, and the charts proved their worth in court when the perpetrator was eventually successfully prosecuted.)
There was an interesting meeting in the late 1980s with the Director of the Hong Kong Independent Commission Against Corruption. He said he very much regretted that we had gone to the Police Force before visiting him, as INDEPOL would have been ideal for his work. But, since his outfit’s main focus was against corruption within the Royal Hong Kong Police Force, he clearly couldn’t be seen to use the same software.
The Queensland Police Service, based on its previous experience with CAFS 800 quickly put INDEPOL to very good use in a number of areas. They were the first people to link INDEPOL to a geographical system, with which they plotted where burglaries had been taking place during office hours in a succession of suburbs off the main road between Brisbane and Surfers’ Paradise. They were able to deduce where the gang were likely to strike next, were ready and waiting when they turned up right on cue, and bagged the lot of them.
The main target of the Australian Customs system was - as one might expect in Australia - various forms of fraud, but a lot of effort was continuously devoted to the ongoing war against drugs. They also had a lot of work to do to combat organised illicit immigration, particularly from Indonesia into the north western coast of Western Australia. Trade in endangered species was also high on the list.
Also in Canberra in the mid-1980s, there was a meeting with a party of spooks from some federal intelligence agency, who subsequently may or may not have developed an INDEPOL system. What was noteworthy was that, at the start of the meeting, they all handed out business cards, which we duly collected. It was only later that we saw that their names were given as Gary Cooper, Clark Gable, Spencer Tracy, Errol Flynn, and the like.
One of the largest financial investigations undertaken with INDEPOL involved the Tricontinental Bank (usually abbreviated to TRICO), a merchant bank owned by the State Bank of Victoria, in Australia.
The Australians had a pretty poor view of merchant banks from early times. This quote from Governor Lachlan Macquarie in 1810 sums it up: “petty banking has thrown open a door to frauds and impersonations of a most grievous nature to the country at large. The persons principally concerned in this nefarious practice are to be found among the lowest orders of society. Such being the credulity of the people that notes of hand issued by these wretches are taken and passed into free circulation as if guaranteed by the best securities”
TRICO had a Managing Director - Ian Johns - who sought to make lots of money for himself and his friends by lending large sums of State Bank money on the security of the shares that were bought with the loans. This was fine as long as prices were going up, but not when they went down as they did in the late 80s. TRICO collapsed, bankrupting its parent Bank and therefore effectively bankrupting the whole State of Victoria. When the dust settled, a Royal Commission of Enquiry was set up to enquire into the matter.
ICL won the IT support contract with INDEPOL, and a small team of ICL staff (including Martin Wright) was set up in the Commission’s offices in Melbourne, with a small 2900 mainframe and a network of terminals for use by counsel and Commission officers.
Main information sources included:
Usage included an immense amount of research - who did what, where, when, how much, and what evidence existed to prove it. Also, during court proceedings, the lawyers had direct access to the transcript of all evidence given up to the end of the previous day, enabling them to ask very searching questions of the form: “yesterday you said ....., today you say ......, while the documents show ..... Please explain.”
There was very good user reaction, with the conclusion that the Commission of Enquiry could not have functioned without the system.
ICL in Australia used INDEPOL in other similar enquiries (the Australians seemed to have plenty of financiers with interesting concepts of truth and honesty).
INDEPOL was also very successfully demonstrated in the analysis of claims against a major motor insurance company in Melbourne. The system immediately threw up the interesting fact that every household in a particular street in the suburbs (Ramsay Street?) had made a claim for whiplash injury and used either the same solicitor or the same doctor or both. This looked likely to be another sale for the software, until the company’s distraught representatives said that this one enquiry session had thrown up enough business to keep their prosecution department busy for two years, and they couldn’t afford the risk that the software might find even more.
“Total Border Protection” is the motto of the New Zealand Customs Service. It quickly developed three very effective INDEPOL applications:
Together these systems contributed to the claim that NZC had kept the country largely free of imported drugs, with local addicts being dependent on home-baked substances.
By contrast, Botswana is one of the nicest countries in Africa, unfortunately now ravaged by AIDS. Its people are peaceful, democratic, and friendly (provided you are not a Boer) and relatively rich from diamonds and beef. Both authors had the good fortune to be sent there several times on INDEPOL-related business
The government and legal system had been designed on the Westminster model. In the early 90s there was a central government computer system on an ICL mainframe and a national telecoms outfit (called BT) with some of the bad habits of a different BT.
The crime rate was relatively low, certainly compared with South Africa. Staff moving from Johannesburg to Gaborone found that at first their children would not go to sleep at night because there were no bars on the windows (and no barbed wire, high walls and armed response units). However, the police performance needed improving.
There was absolutely no interest in what systems the neighbouring South African police were using. That was scarcely surprising as, only a few years earlier, South African forces had been shooting up Gaborone on a regular basis in hot pursuit of the ANC - (there are still bullet marks on the Central Police Station). Instead, the Botswana Police looked to the UK and in particular the Lancashire Constabulary Crime Recording system.
A small team was sent from UK (INDEPOL only needed small teams). It was never clear how Martin Wright became PM for the project. Some changes were needed to the Lancashire system to encompass Botswana legal niceties. For example, they had a three level court system - crown, district, and tribal. Fines were payable in four currencies - pula (local), rand, dollar or sterling. A sentence of corporal punishment included details of which instrument should be used to administer it. And there were special features of local traffic laws - for example, it was illegal to have more than three donkeys abreast pulling a cart.
It was a major task to train input staff and enquiry operators. Botswana people were highly educated but had never seen a computer. The training consultant started by carrying a keyboard around the training room, demonstrating that if you pressed the A key you got an A, but by the end of the first week they were all playing solitaire like old hands. They very rapidly became excellent operators.
There was a great problem getting a link from the Police Training College to the mainframe. BT were nagged and nagged with no effect. But at last one morning at 8:30, the link was found to be working. Unfortunately, at 9:00 there was a furious call from the Finance Ministry, who wanted their line back. BTs are the same the world over!
The system went live after 12 months and had its first successful arrest after two weeks. Thereafter it continued happily and successfully until, several years later, the government moved away from mainframe computing.
Conclusion
It’s sad that ICL never managed to capitalise sufficiently on the performance advantage which CAFS provided. Many ICL people knew how to make computers and how to sell them, but relatively few understood what they were used for. A constant theme throughout these accounts of successful CAFS installations was that the end users knew what was good for them and often pushed hard to obtain it. The IT manager might be obsessed with going distributed, or standardising on UNIX, or whatever the current technical fad might be, but the users knew they wanted a fast, responsive and flexible enquiry service and insisted on having it. There’s no data on how many CAFS units there may still be in the world, or in what form they are currently implemented, but it is very satisfying to both authors to know that after more than 20 years there were still, at the end of 2007, more than seven INDEPOL services running.
Editor’s note: This is an edited transcript of part of a talk given by the authors at the Science Museum on 18 October 2007. Contact Hamish Carmichael at hamishc@globalnet.co.uk.
| Top | Previous | Next |
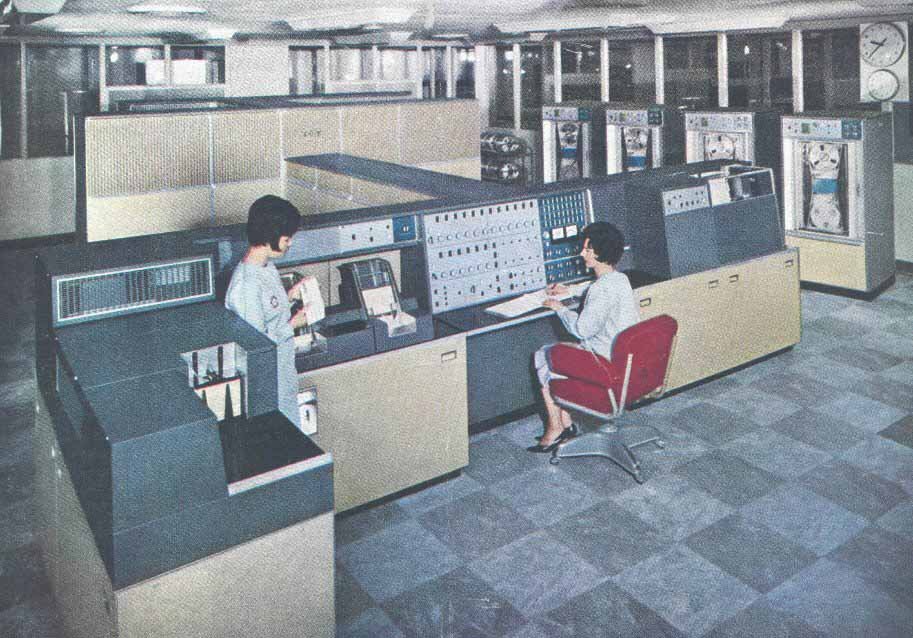
Rod Brown gives us an update on “Flossie” - the ICT 1301 living in a barn in Kent, first introduced to us by Hamish Carmichael in Resurrection 21.
 |
|
A publicity shot of an ICT 1301 at John Lewis |
During a visit from the CCS on the 11th Februry 2009, Dr David Hartley was kind enough to refer to the 1301 preservation project as an “heroic undertaking”. He is, of course, correct. Any project to restore any piece of computing history from software to hardware, including emulation of now extinct machines, requires a lot more work than first estimates seem to indicate.
This is a report on the status of a project that is about to enter its sixth year of hands-on working and is very close to its seventh year of implementation. In common with all the other equally important projects out there, when we started we were too foolish to work out that we could not achieve what we wanted to do, so we went ahead and did it anyway!
A website exists for this project and has all the boring technical bits on it for those who wish to know. But the story of this specific machine and its place in British computing history is the main driver of the work that has been undertaken to get this far, and of its all important interaction with its supporting public!
When the designer, Dr Bird, visited the project in 2004, we were overjoyed to discover, not only the story behind some of the design considerations, but also the lineage of the design within the history of British computing. The 1301 shares a concept that is carried forward from the likes of the punched card calculating machines such as the ICT550/555 in that it too goes part way to allowing the non-binary coding of its operator / programmer interface by being a binary coded decimal (BCD) machine, designed as 12 BCD digits per 48 bit word. The design is implemented in germanium transistors and diodes on discrete logic boards which, due to their age, feature a very open layout and hence are easy to work on and repair, on a board by board basis. Positioned as industry workhorses rather than high specification special application machines, over 150 machines of type 1300/1301 were produced (I do have some evidence of serial number 179 somewhere so it may be more!). The distinction held by our particular machine however, is the fact that it was the first of its type to be installed in 1962 and, as serial number six (all previous machines were prototypes), even this machine needed many field-fitted modifications before it was fully functional.
The end of the series was the 1302, of which only a limited number was ever made. But the 1302 provided the development of, and test bed for, an interactive typewriter-driven operating system called Executive, as well as the implementation of a standardised peripheral interface. Both these developments span the transition to the 1900 range, the latter destined to become known as the 1900 Standard Interface.
The limitation of the 1302 executive was just three running applications and a slot zero for Executive. However, to timeshare system resources with even three programs, all co-existing in 16k of store, was a milestone in the life of the series. So the 1300 series does slot neatly into the history of British computing. My last technical role in ICL was as a consultant on Series 39. The wait from the point of powering up a freshly connected macrolan installation to the point where the operating terminal cleared and offered to run a job to set up the system under George was a good time to reflect on that lineage; from 1300 to 1900 through 2900 and then Series 39.
In general, the 1301 hardware was overbuilt and that has contributed to its ability to survive 47 years so far. Availability of spares is not an issue as Roger Holmes, the owner, very wisely purchased more equipment than was needed during his acquisition phase of the machine’s life. The only downside to this is that the factory at GEC which undertook the initial production also produced telephone exchanges. So one of the features of the machine is that all of the logic board connections are made by wrapped wire wound over two adjacent pins and as there are up to 25 pins per logic package, a quick change of a failing board is not as easy as with conventional plug-in boards. The upside, however, is that, as we now enter the 47th year of this machine’s life, we observe that, had these connections been implemented as either tinned copper or even gold plated connections, their reliability would now be so bad that we might never have achieved the task of restoring as much as we have.
Because of the above, and like all of the other conservation/ resurrection projects running, we were in need of specialised tools to allow us to work on this machine. The only source for these tools was to contact retired engineers and other users and to publicise the project in the hope that enough of these tools could be located. This is where this project started to acquire its public face. The response over the years to the existence of a website that mentions a piece of UK computing history had taught us the power of advertising our existence. Sufficient tools were found and freely donated to the project, usually with wishes of good luck in completing the restoration, sometimes with warnings about what we were trying to achieve and its sheer impossibility!
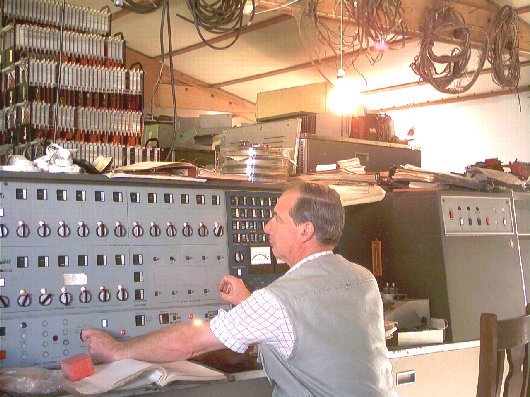 |
|
Set the Controls for the Heart of the Sun! |
Again, we have stuck to the foolish path and just kept going. So that, in its seventh year, we believe that we have about 91% of the electronics restored to a working state (temperature and environment permitting). We also have over 50% of the peripheral devices working! But, I refuse to say whether that is all of the devices only half working or only half of the devices fully working. On a day by day basis, either could be true. As such, I am sure you will all recognise this as part of the joy and tears experience of ongoing computer conservation.
The public face of the project has also resolved one of the other problems that we share with other conservation projects. We have to operate within a very tight budget. The machine consumes 13 kw of three phase power and is not cheap to run. The ongoing need to buy fuses, lamps and even the wire to make connections has to be funded. Blank paper tape, boxes of listing paper, ribbons for the printer, reels of solder and even parts to allow us to capture the recovered software, all need to be funded. As such, we approached the concept of opening the doors to the public with caution, just to judge the response to a 42 year old working computer. Now, after four public open days, we have grown our supporter base and even earned a little in the sale of mementos and small items on the day. Not a fortune it is true, but enough to make the difference and keep us moving forward. That, coupled with showing off the machine to over 1000 people of all ages, makes us feel we must be doing something right. The public’s response to being allowed to walk through a hot noisy working computer installation, when most people’s experience has been limited to clicking on desktop icons, is most positive! In 2009, Roger has enhanced the access and space around the machine and the experience is designed to be very immersive. Short of actually taking visitors back 45 years, it’s as close as we can get!
By just existing, we have been able to organise open days for engineers and fly the flag for ongoing computer conservation in general. The last Computer Conservation Society Visit was in 2005 and you are welcome to organise another visit! May 2009 finds us hosting a visitor from New Zealand as well as the open day in July. Which, for a machine which has been sold as scrap twice in its life, is not too bad. We are in touch with other projects around the UK and overseas, some of which have hardware machines to restore and others which are just software based, but which, nonetheless, are making great strides in resurrecting our collective past.
We hope to continue and, in 2012, the machine will clock up its 50th birthday. So, between now and then, visit www.ict1301.co.uk and see Flossie′s website to read the latest stories about our failures and victories. View some of the growing sets of online documents we are publishing and know that, as computer conservationists, you are not alone. We are, after all, part of the ‘Our Computer Heritage’ Project and are trying to ensure people know about the project and our existence. We are only too happy to collect visitors and categorise them as engineers, programmers, operators or just plain members of the public who want to come along and say hello! We also do a little bit of reconnecting people with the past, as well as inviting them to provide brief stories from the past themselves. After all, they typed “ICT 1301” into Google or Yahoo and need to be rewarded for doing that!
Now, to complete this update, I started by saying that we were following a foolish path. Well, it would seem we are nearing many of our targets. At some point we may become “heroic” if we actually arrive at our destination. But being who we are, we just might start on some other foolish project and enjoy ourselves all over again.
Editor’s note: Rod Brown is the webmaster of www.ict1301.co.uk. The project can be contacted at flossie@ict1301.co.uk.
| Top | Previous | Next |
King’s College London is fortunate in having a small museum of computing technology artefacts, together with staff members with the knowledge and enthusiasm to make it worthwhile.
Abstract
In an ever-expanding, technology-driven university curriculum such as Computer Science, it is not always feasible to reserve a place in the academic timetable for a lecture course on the history of computing. Nevertheless, it is important that both undergraduate and postgraduate Computer Science students realise that their chosen subject did not begin with the PDA or the WWW. In an attempt to put modern digital systems into their historical and technological contexts, the Department of Computer Science at King′s College London has gradually built up a collection of around 100 mechanical, analogue and digital computing artefacts. During September 2008, they were cleaned, professionally catalogued, photographed and re-labelled. The degree of student interest generated by the refurbished museum display has been gratifying.
Introduction
The Department of Computing (as it was originally named) was established in its present home in the Strand campus at King’s College London in mid-1987. The decision to form the Department arose from a series of institutional mergers within the University of London during the mid-1980s. The Computer Science staff of Westfield College, which was merging with Queen Mary College, were transferred to King’s College, which was simultaneously merging with Queen Elizabeth College and Chelsea College. A Professor and a Lecturer were appointed under the auspices of the then government’s “New Blood” I.T. initiative.
Two further academic staff members were transferred to the fledgling Department from King’s College Computing Centre. The first Head of Department, Professor John Buxton, actively encouraged the idea of bringing together a corpus of historic computing artefacts in the heart of the department where they could be displayed to advantage. His previous appointment at the University of Warwick, with its successful History of Computing course, may well have been influential in this respect. A number of colleagues, including Andrew Wells (ex- STC), Peter Lee (ex-Plessey), Alan Fairbourn (ex-Institute of Computer Science), Simon Fairthorne and Brian Meek (both ex-QEC) had access to early manuals, photographs and actual equipment that formed an initial nucleus around which the collection has gradually grown by accretion over the following two decades.
The Display
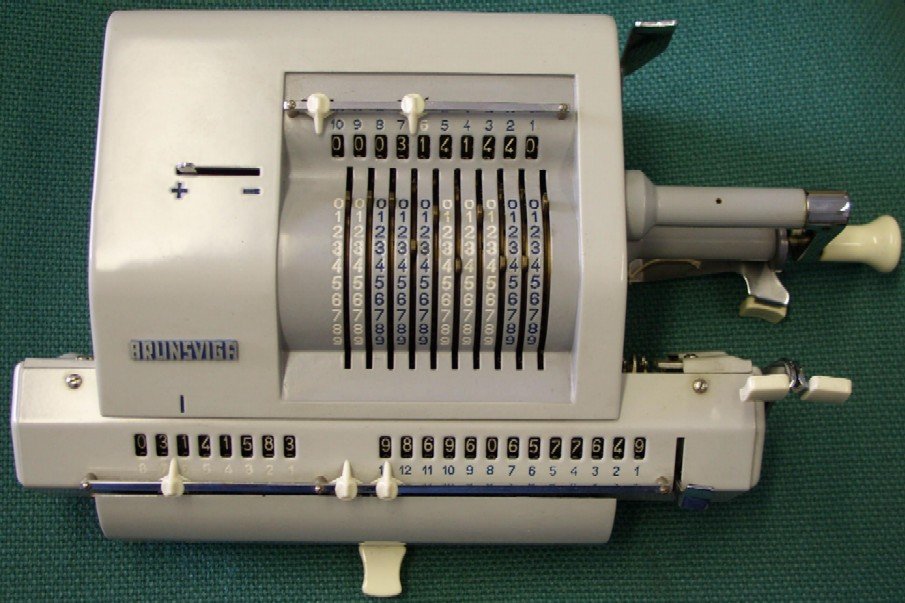 |
|
Brunsviga barrel adder |
The Museum is installed in 16 top-lit, lockable display cases running along the central corridor of the Department. The original design for the display was based upon a sequence of themes: early days, input media, main memory, backing store, the shrinking computer, and miscellaneous. However, some informal “market research” amongst the current cohort of students suggested, perhaps surprisingly, that a chronological approach would be better appreciated. Hence the recently refurbished display maintains an essentially linear chronology as one proceeds along the corridor. However, when describing the collection verbally it is more convenient and natural to use the original thematic taxonomy.
The Artefacts
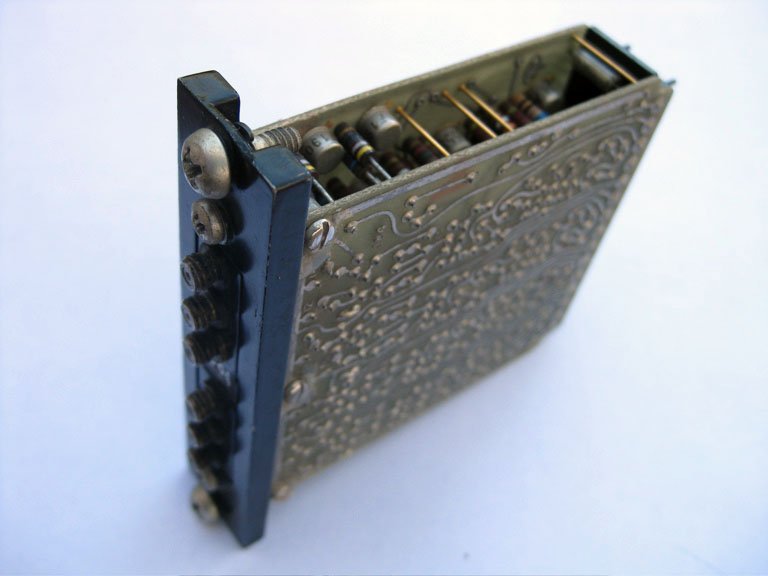
 |
|
Cipher machine |
The pre-electronic era is represented by Chinese (suanpan) and Japanese (soroban) abacuses, helical and linear slide rules, a Jacquard loom card, a Brunsviga “barrel adder” and its electrical counterpart the Munroe electric calculator, together with a US Army Signal Corps M-42 converter (i.e. cipher machine).
Input media includes IBM 80-column and 96-column punched cards together with a steel card gauge, an IBM Port-a-Punch with perforated cards and stylus, and a hand cardpunch. These are accompanied by 8-hole ASCII paper tape with paper tape splicing equipment (stylus and patches). Currently we have no examples of 5-hole Baudot paper tape. [This omission has now been remedied courtesy of the Pegasus team: ed.] A General Electric PTR66G optical paper tape reader dated 1970 is also on display. An unusual item is a 1966 computer-readable election ballot form from Multnomah County, Oregon, USA.
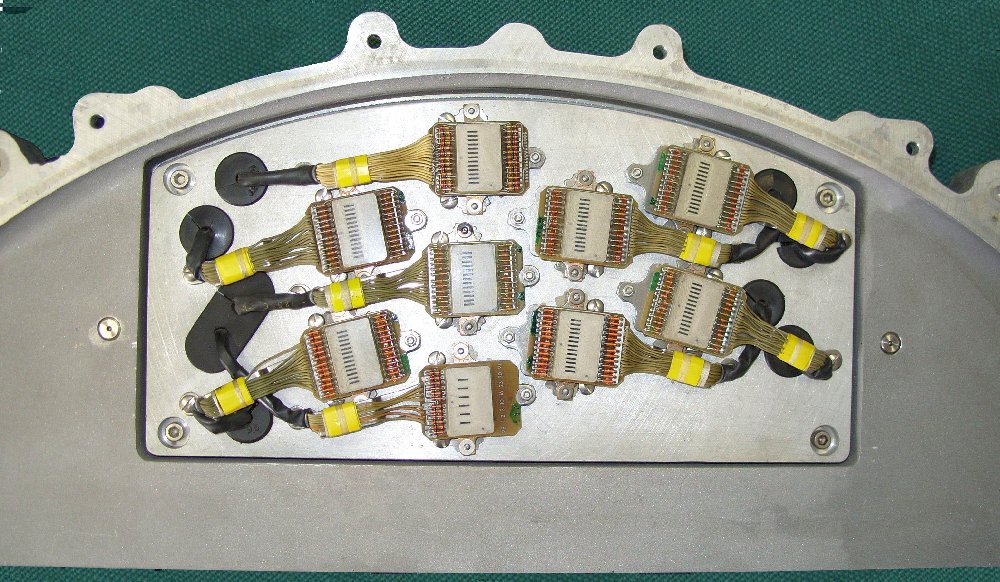
 |
|
CDC “cordwood module” |
The main memory category also includes central processor technology. Here may be found a “cordwood module” of the Y-register of a CDC 1700 to illustrate discrete silicon transistors, and the diode decoding matrix and associated driving circuitry of a CTL Modular One CPU. A magnetostrictive nickel delay line, and two examples of core store (one of which is thought to be from the London University Atlas 1) can also be seen, together with a Toko plated wire memory module. A set of fluidic logic gates by Plessey for use in electronically hostile environments is a relatively unusual item.
 |
|
Fixed disc heads |
Examples of backing store include 7-inch (PDP), 5.25-inch (BBC), and 3.5-inch (IBM PC) floppy discs, together with an opened-up floppy disc drive. The read/write heads of a CTL Modular One fixed disc and a CDC exchangeable disc pack are also on view. A reel of magnetic tape and a cartridge tape are included in this category.
The shrinking computer is concerned with examples of chip technology. On display are examples of the Z8002, Intel 4040, Intel 8080/8085, Motorola 68000/68020, IBM 4300 and Transputer T414 processors.
The earliest example of a complete machine is the 1976 DEC LSI-11/03. We are fortunate to have 3 early personal computers on display: a 1986 Apple Macintosh SE, a 1981 BBC Model B with dual floppy disc drive and user manuals, and a 1981 IBM PC. These machines are complemented by a collection of early hobbyist computer magazines including issues of Computing Today and Personal Computer World dated between 1979 and 1981.
The account of the artefacts given above is indicative and illustrative only. It is not intended to be complete or comprehensive
Educational Opportunities
We have been exploring a number of ways to exploit the collection educationally. It has already been used to illustrate various aspects of computer hardware as it relates to our Computer Architecture course, most notably by Henry Norton. The professional requirement that all students must be capable of writing clearly expressed and properly structured technical reports has given rise to a proposal to use the collection as a basis for training students in this discipline. In the not-too-distant future it may also be possible to mount a joint final year undergraduate/postgraduate taught course in computer history as an option which will be able to make extensive use of the artefacts in the collection to illustrate technological trends over the 60 years of the digital electronic computer, and its antecedents.
Visiting
Visits to the Computing Museum at King’s College London may be arranged by contacting the Curator, Dr Richard Overill (020 7848 2833, richard.overill@kcl.ac.uk). Individual visitors can be accommodated at most times of the working day. Groups of more than three visitors should aim to arrange their visits to coincide with university vacations if at all possible.
Contact detailsReaders wishing to contact the Editor may do so by email to |
| Top | Previous | Next |

| Top | Previous | Next |
Harry Johnson’s advent on the computer scene was an example of the phenomenal persuasiveness of Vivian Bowden. Harry has told how Bowden met him at the dining room of a London station and, by the end of the evening had persuaded him that his talents would be wasted in the Scientific Civil Service and that he would fly higher in this new world.
After Bowden had persuaded the Ferranti management that there was a world beyond the boundaries of glorious metropolitan Manchester, Harry joined me in London. Soon Conway Berners-Lee joined too. The three of us set up a computing activity in a hired room of a London hotel. This grew to become the Ferranti Computer Centre.
Harry was something of a polymath and able to turn his skills to many directions. During the early years of Ferranti’s computer activities, he applied queuing theory to air-traffic and airport design problems, and later played a large part in setting up the commercial data-processing systems around the Perseus computer.
The Atlas computer involved a combination of hardware and software techniques, each inter-dependent upon the other, which were at the limits of what was then possible and were done by separate groups. Johnson was given the task of bringing those together. While we have had to become accustomed to calamitous major computer projects, his capabilities ensured that, from a user’s point of view, Atlas became an outstanding success.
At one stage, Johnson was president of the European Computer Manufacturers’ Association (ECMA). Working in close partnership with Peter Dorey, they built up what had been the Ferranti Computer Laboratory at Bracknell into the very substantial company Ferranti Computer Systems Ltd. Johnson became its Sales and Technical Director, in charge of planning and marketing its products. It specialised in industrial process-control systems, military and air-traffic control applications that required a reliability and freedom from malfunction far beyond the norm for other branches of computing.
Johnson had a clear memory of the early days of computing and an exceptional grasp of the essentials of the situations in which he was involved. Outwardly, these were very often confused and multi-faceted. His passing is a severe break with that fascinating epoch.
| Top | Previous | Next |
Dr. Brian Napper of Manchester University’s Department of Computer Science died in March after a short illness.
Brian joined the Department in 1960 as a member of Tony Brooker’s influential Compiler Compiler team, staying on at the university long after all the other members of the group had dispersed to universities around the world. Brian developed an interest in the history of computing, in particular the story of developments in Manchester, bringing to it a scholarly discipline and a passionate loyalty - “Defending the honour of the Department” as he once put it to me at a CCS meeting in London.
In 1998, Brian and wife Hilary Kahn (Obituary Resurrection 43 ) were the driving forces behind Computer 50, a celebration of the 50th anniversary of the first stored-program computer at Manchester. Brian’s website www.computer50.org is not only a permanent record of the events of that wonderful occasion, but a comprehensive history of Manchester computer developments complementing Simon Lavington’s earlier work.
Brian’s final contribution was the profile of Tony Brooker in Resurrection 45 , to which he applied his usual erudition and thoroughness.
The Computer Conservation Society has lost a good friend who will be much missed.
North West Group contact detailsChairman Tom Hinchliffe: Tel: 01663 765040. |
| Top | Previous | Next |
MOSI : every Tuesday at 12:00 and 14:00 Demonstrations of the replica Small- Scale Experimental Machine at the Museum of Science and Industry in Manchester.
Bletchley Park : daily Guided tours and exhibitions, price £10.00, or £8.00 for concessions (children under 12, free). Exhibition of wartime code-breaking equipment and procedures, including the replica Bombe and replica Colossus, plus tours of the wartime buildings. Go to www.bletchleypark.org.uk to check details of times and special events.
Science Museum : alternate Wednesdays 11:00 to 15:00 Pegasus “in steam” day. The first date in 2009 was 14th January.
23 April 2009 “JANET - the First 25 Years”.
14 May 2009 “BBC Domesday Book Project”.
London meetings take place in the Director’s Suite of the Science Museum, starting at 14:30. The Director’s Suite entrance is in Exhibition Road, next to the exit from the tunnel from South Kensington Station, on the left as you come up the steps. Queries about London meetings should be addressed to Roger Johnson at r.johnson@bcs.org.uk , or by post to Roger at Birkbeck College, Malet Street, London WC1E 7HX.
15 September 2009 “Iconic Machines : Exhibiting a History of Computing” Doron Swade.
20 October 2009 “The Evolution of Hard Discs” Neil Macphail.
North West Group meetings take place in the Conference Room at the Manchester Museum of Science and Industry, usually starting at 17:30; tea is served from 17:00. Queries about Manchester meetings should go to William Gunn at william.gunn@ntlworld.com.
Details are subject to change. Members wishing to attend any meeting are advised to check the events page on the Society website at www.computerconservationsociety.org for final details which will be published in advance of each event. Details will also be published on the BCS website (in the BCS events calendar) and in the Events Diary columns of Computing and Computer Weekly.
| Top | Previous | Next |
[The printed version carries contact details of committee members]
Chairman Dr David Hartley FBCS CEng
Vice-Chairman Tony Sale Hon FBCS
Secretary, Chairman DEC Working Party Kevin Murrell
Treasurer Dan Hayton
Science Museum representative Dr Tilly Blyth
TNA representative David Glover
Bletchley Park volunteers representative Pete Chilvers
Chairman, Elliott 803 Working Party John Sinclair
Chairman, Elliott 401 Working Party Arthur Rowles
Chairman, Pegasus Working Party Len Hewitt MBCS
Chairman, Bombe Rebuild Project John Harper Hon FBCS CEng MIEE
Chairman, Software Conservation Working Party Dr Dave Holdsworth CEng Hon FBCS
Chairman, ICT 1301 Working Party Rod Brown
Digital Archivist & Chairman, Our Computer Heritage Working Party
Professor Simon Lavington FBCS FIEE CEng
Editor, Resurrection Dik Leatherdale MBCS
Web Site Editor Alan Thomson
Archivist Hamish Carmichael FBCS
Meetings Secretary Dr Roger Johnson FBCS
Chairman, North West Group Tom Hinchliffe
Dr David Anderson
Peter Barnes FBCS
Chris Burton CEng FIEE FBCS
Professor Martin Campbell-Kelly
George Davis CEng Hon FBCS
Peter Holland
Dr Doron Swade CEng FBCS MBE
Readers who have general queries to put to the Society should address them to the Secretary: contact details are given elsewhere. Members who move house should notify Kevin Murrell of their new address to ensure that they continue to receive copies of Resurrection. Those who are also members of the BCS should note that the CCS membership is different from the BCS list and is therefore maintained separately.
| Top | Previous |
The Computer Conservation Society (CCS) is a co-operative venture between the British Computer Society, the Science Museum of London and the Museum of Science and Industry in Manchester.
The CCS was constituted in September 1989 as a Specialist Group of the British Computer Society (BCS). It thus is covered by the Royal Charter and charitable status of the BCS.
The aims of the CCS are to
Membership is open to anyone interested in computer conservation and the history of computing.
The CCS is funded and supported by voluntary subscriptions from members, a grant from the BCS, fees from corporate membership, donations, and by the free use of Science Museum facilities. Some charges may be made for publications and attendance at seminars and conferences.
There are a number of active Working Parties on specific computer restorations and early computer technologies and software. Younger people are especially encouraged to take part in order to achieve skills transfer.
| ||||||||||