 Infrastructure Model
Infrastructure Model  Infrastructure Model
Infrastructure Model This slide was not used.
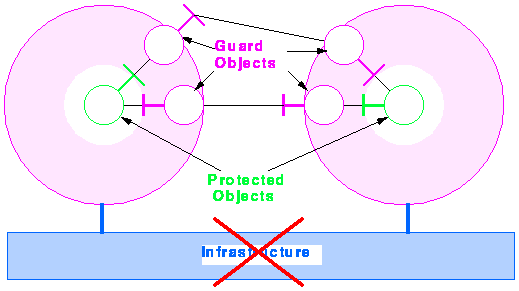
The diagram illustrates the encapsulation and controlled interaction principles. Identify and enforce the protection boundaries with controls on the interation paths - rather like a firewall approach but with finer granularity. Beware of global trusted infrastructure assumptions, and especially any approach that shows an infrastructure spanning domains of authority.
Note the similarity of the protected object and the composite of the object and its guards. This approach allows nested protection domains. The security mechanisms can be transparent to the protected objects; current WWW technology does not work like this, but there is nothing to prevent it being implemented this way. The guard objects may be generic or specialised to the service; a specialised guard may be a composite of generic and specialised components.